Ventoy is a free and open-source tool for creating multiboot USBs. It’s one of the best alternatives to Rufus thanks to its excellent compatibility and ease of use.
One of the main complaints users had regarding Ventoy was that Ventoy drives wouldn’t boot onsecure boot-enabled systems. The devs patched this in version 1.0.07, so you may create drives that work with secure boot now.
You’ll encounter a “Verification failed: (01XA) Security Violation” error when booting such drives for the first time. This is an intentional one-time error. I’ll explain how you may get past it in this article.
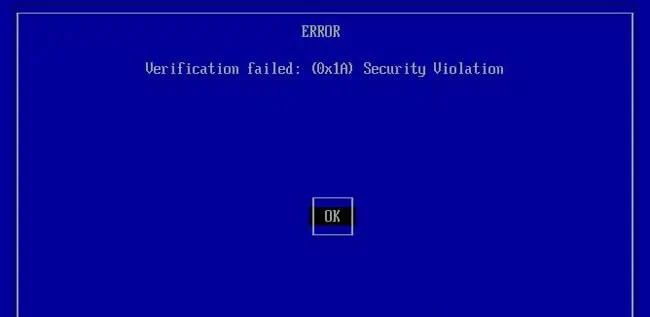
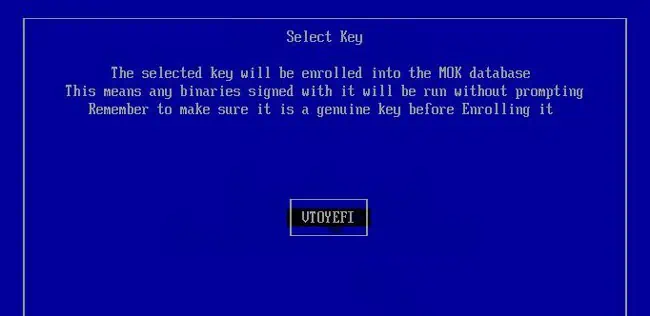
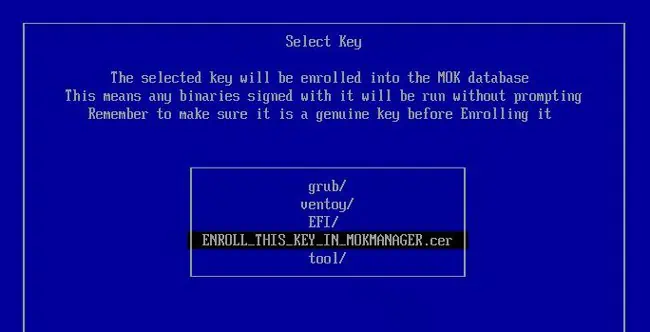
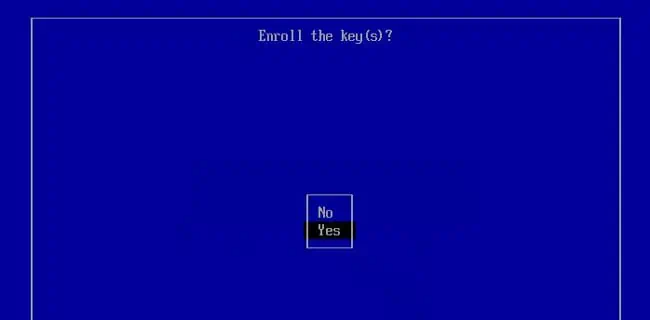
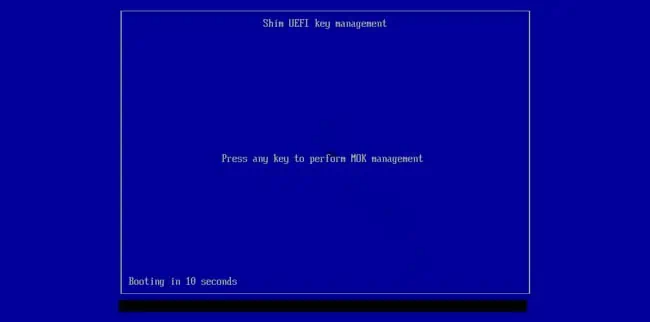
One of the ways Ventoy can work with secure boot now is by adding Ventoy’s key as a trusted key to the Machine Owner Key (MOK) database. To add secure boot support with this method,
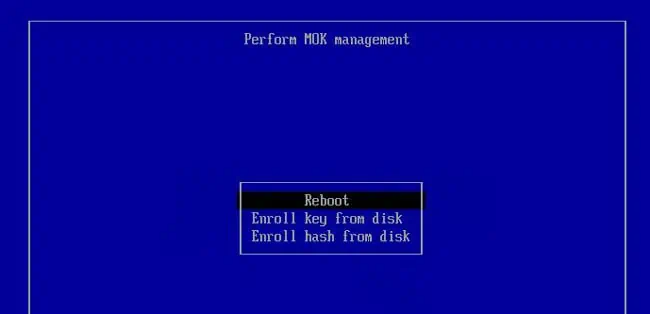
Enroll Hash from Disk
An alternative way to enable secure boot support for Ventoy is by trusting the current version of the bootloader (i.e., enrolling a hash). I recommend enrolling a key instead of this as you may have to perform this process again after updates to the bootloader. However, if you prefer this method, here are the necessary steps:
Disabling Secure Boot
Secure Boot support is enabled by default since Ventoy 1.0.76. On older versions, this option needs to be manually enabled.
If you created a drive without enabling this option, you may run Ventoy again, enable it now, then update the drive. This’ll make the drive compatible with secure boot without making any changes to the files on the drive.
If you want to boot a Ventoy drive that doesn’t have this option enabled, the only way is todisable secure boot.
In rare cases, even drives with this option enabled may lead to a different error than the one we covered here. Once again, your only option in such cases is to disable secure boot entirely. Here’s how you may do this:

After rebooting, you should be able to boot with the Ventoy drive as secure boot is disabled now.